Black box pentest
- Mimic a true cyber attack. Most realistic.
- Zero access or internal information.
- Time consuming and more likely to miss a vulnerability.
A vital, compliance-driven penetration test designed to secure the COVID QR code issuance system. Specifically mandated by the Dutch Ministry of Healthcare, this test ensures public safety in establishments during pandemic times.
CoronaCheck Pentest stands as a pivotal cybersecurity gatekeeper for Covid Labs. Earning the ability to issue QR codes hinges on passing this thorough assessment, mandated by the healthcare authorities.
This specialized test not only ensures technical compliance but symbolizes the unwavering commitment to public safety. By fortifying the QR code issuance mechanism, it instills confidence and trust in public health measures.

CCV Standard Compliance: Our penetration testing rigorously aligns with the CCV's stringent requirements for comprehensive security evaluations.
Norm-Conforming Documentation: Each test is meticulously documented, adhering to CCV norms for transparency and precision.
Guaranteed Quality Testing: Clients are assured of receiving top-tier penetration testing services, validated by our adherence to CCV standards.
Expert Team with OSCP Certification: Every security specialist on our team holds an OSCP certification, ensuring depth and expertise in our testing processes.
From within your network, our internal pentest dives into the CoronaCheck-App. We focus on server-side vulnerabilities, safeguarding data and processes against internal threats.
Probing from the inside, our experts pinpoint vulnerabilities that could be exploited by insiders, ensuring that health data remains uncompromised and consistently secure.
Evaluates vulnerabilities from the perspective of an internal attacker
Often more costly due to the requirement of a steady in-house security team
Facilitates consistent security maintenance through regular assessments
Potentially more comprehensive as it accounts for threats from both internal and external sources
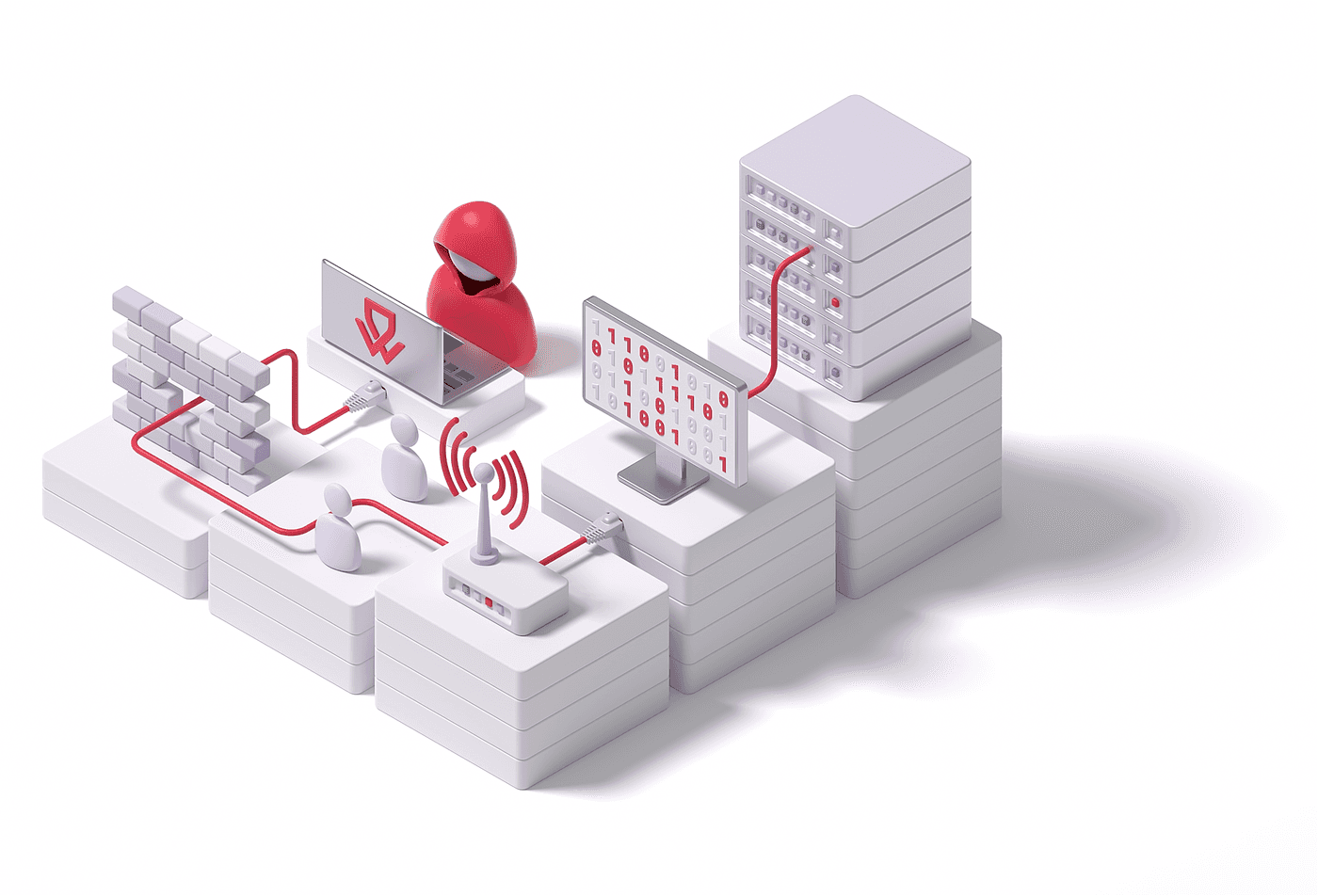
Our external pentest approaches the CoronaCheck-App from a public perspective. We test interactions with outside systems, defending against broad internet threats.
Every external component is methodically tested, guarding the app against potential breaches, ensuring secure data exchange, and protecting user information at all touchpoints.
Evaluates vulnerabilities from the perspective of an external attacker
Can be more budget-friendly as it allows for outsourcing and does not necessitatea constant team
Typically conducted periodically with proper planning
Generally less comprehensive as it mainly focuses on external threats
Our experts will help you!
The methodology for our CoronaCheck Pentest strictly adheres to the guidelines outlined in the PTES Standard Framework. Below is a step-by-step breakdown of our comprehensive pentesting approach
Obtaining essential data and insights that will inform the strategy for the subsequent phases.
Identifying potential threats and developing scenarios to test the vulnerabilities.
Scrutinizing the system to find vulnerabilities that could potentially be exploited.
Actively exploiting found vulnerabilities to assess the possible damages and risks.
Creating a concise report with a timeline detailing actions, vulnerabilities identified, and suggested countermeasures.
Conducting follow-up tests to ensure all vulnerabilities have been adequately addressed.
