Black box pentest
- Mimic a true cyber attack. Most realistic.
- Zero access or internal information.
- Time consuming and more likely to miss a vulnerability.
In-depth evaluation of web applications, aimed at discovering potential vulnerabilities or weaknesses. This service ensures robust protection for businesses operating online, keeping user data safe.
Web Application Pentesting, also known as Web-App Pentest or WEB-VAPT (Web Vulnerability Assessment / Penetration Testing), is a comprehensive security assessment that focuses on online platforms. Through thorough analysis, experts identify hidden vulnerabilities, offer mitigation strategies, and ensure that digital interfaces are robust against web-based cyber threats.
In today's digital age, a Web Application Pentest isn't a luxury; it's a necessity. It offers businesses a clear insight into their online security posture, ensuring customer trust, and protecting digital assets. Make your online presence resilient, secure, and trustworthy.

CCV Standard Compliance: Our penetration testing rigorously aligns with the CCV's stringent requirements for comprehensive security evaluations.
Norm-Conforming Documentation: Each test is meticulously documented, adhering to CCV norms for transparency and precision.
Guaranteed Quality Testing: Clients are assured of receiving top-tier penetration testing services, validated by our adherence to CCV standards.
Expert Team with OSCP Certification: Every security specialist on our team holds an OSCP certification, ensuring depth and expertise in our testing processes.
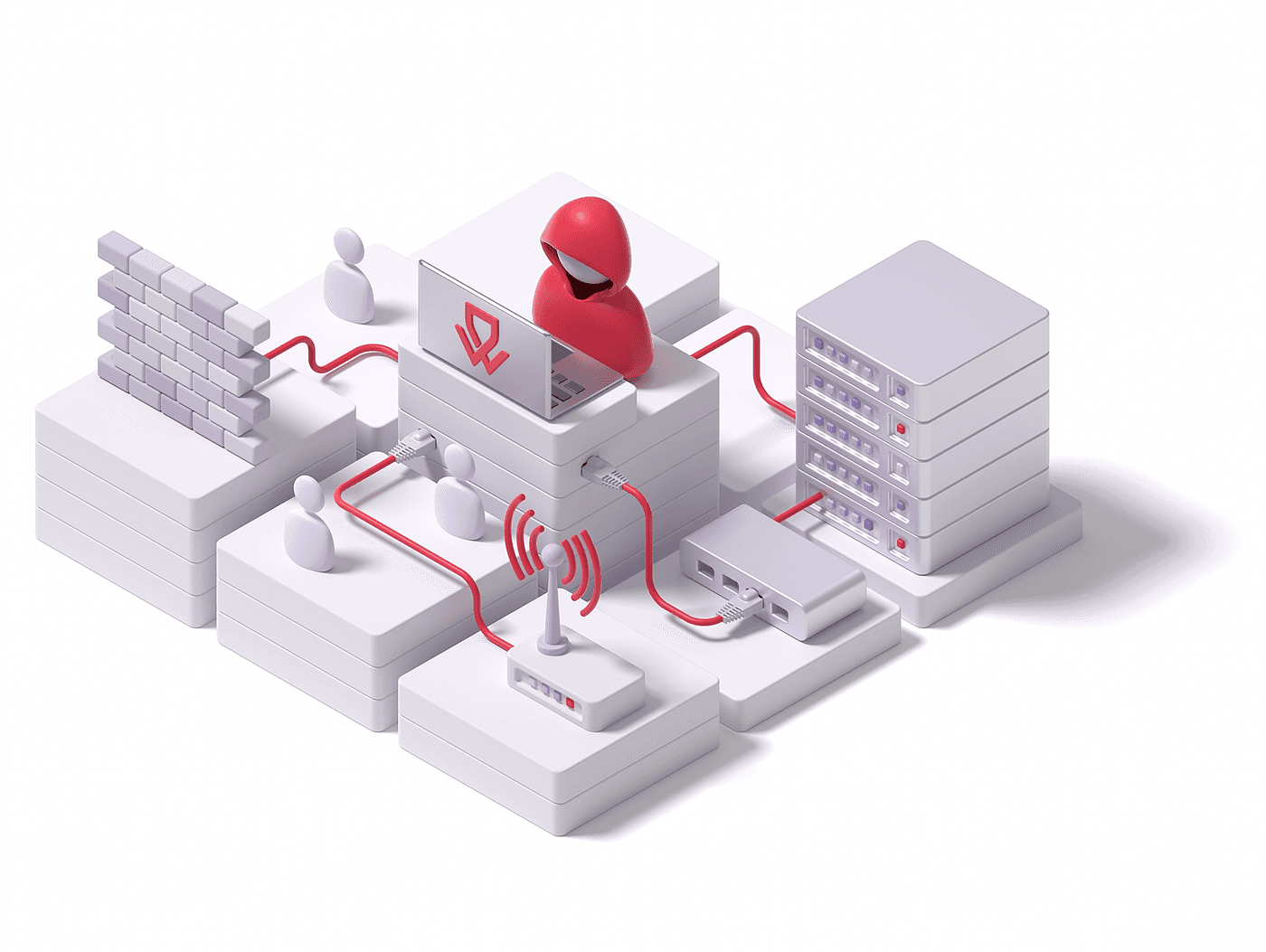
From within the organization, we meticulously dissect web application infrastructures. Delving deep into codebases, we ensure comprehensive protection from internal adversaries.
Our internal assessment prioritizes potential weak spots that might be exploited from inside, ensuring the backbone of your web application remains robust and unyielding.
Evaluates vulnerabilities from the perspective of an internal attacker
Allows for a Larger Scope to Be Tested
Diminishes the Need for VPN or IP Whitelisting
Direct In-Person Engagement between Security Expert and Client
Targeting the interface that the world sees, we assess your application's resistance to external threats. From the vast expanse of the internet, we mimic potential adversaries.
Each public-facing component undergoes rigorous testing, solidifying its defense against a myriad of external cyber threats and potential breach attempts.
Evaluates vulnerabilities from the perspective of an external attacker
Can be more budget-friendly as it allows for outsourcing and does not necessitatea constant team
Typically conducted periodically with proper planning
Realistic Attack Simulation for External Threats
Our experts will help you!

A Web Application Pentest should be scheduled at several critical junctures:
Regular pentesting helps ensure your web applications remain secure and trustworthy.
1. What are the limitations of vulnerability scans in detecting non-standard vulnerabilities?
Vulnerability scans primarily detect known security flaws quickly using automated tools, which may not effectively identify atypical, complex vulnerabilities often explored in pentests.
2. Under what circumstances is a vulnerability scan insufficient?
A vulnerability scan is insufficient when detailed, context-aware testing is required, especially to assess the application against sophisticated or targeted attack scenarios that automated tools may overlook.
3. How do expertise and creative strategies enhance a Web Application Pentest?
Unlike automated scans, a Web Application Pentest relies on the creativity and deep expertise of ethical hackers, who manually simulate attacks to uncover and exploit security gaps that automated tools cannot.
4. What distinguishes the role of ethical hackers in a Web Application Pentest?
Ethical hackers play a critical role in a Web Application Pentest by conducting extensive manual testing, using bespoke tactics and tools to identify vulnerabilities that an automated scan would typically miss.
1. How should the choice of Pentest method be tailored to a web application?
The choice of Pentest method should be tailored based on the web application’s specific requirements, considering factors like user behavior, sensitivity of data, and the architecture of the system.
2. What are the advantages and disadvantages of each Pentest method (black box, grey box, white box) for web applications?
3. How are testing methods like static, dynamic, and interactive analysis applied in Web Application Pentests?